 Growing concern about deep-fake videos will make it increasingly important to be able to demonstrate the integrity of video evidence, warn IDIS. Rapid advances in digital video manipulation techniques, and a rise in alleged deep-fake celebrity videos being reported in the news, will put pressure on both video tech users and on prosecutors to demonstrate the integrity of any footage they use says the video technology manufacturer.
Growing concern about deep-fake videos will make it increasingly important to be able to demonstrate the integrity of video evidence, warn IDIS. Rapid advances in digital video manipulation techniques, and a rise in alleged deep-fake celebrity videos being reported in the news, will put pressure on both video tech users and on prosecutors to demonstrate the integrity of any footage they use says the video technology manufacturer.
“As we look ahead, wherever video is presented for use as legal evidence, or as part of internal disciplinary proceedings, we will see more attempts to assert that footage is not genuine. Courts will dismiss evidence where tampering cannot be ruled out,” says Dr Peter Kim, Global Technical Consultant, IDIS. “Any challenge to the integrity of video evidence, if not countered, risks undermining the value of the entire video solution. This is particularly true in applications where investigating and prosecuting wrongdoing is a key function of the camera system. So, it will be vital that users can demonstrate beyond doubt that their footage has not been tampered with in any way.”
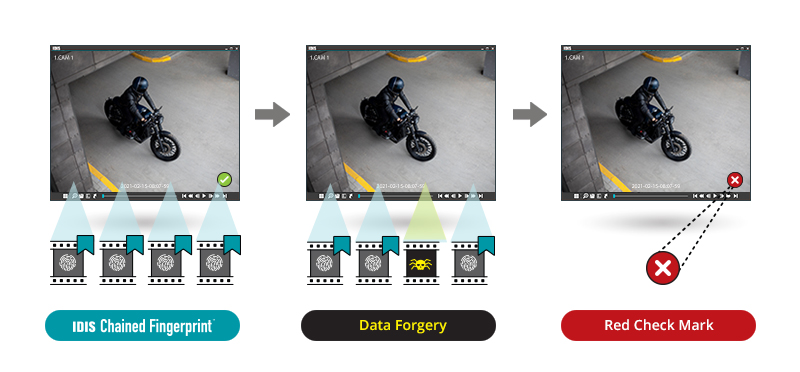
One method of protecting video footage integrity is through the use of algorithms such as Chained Fingerprint, which ensures the integrity of the recorded and exported video data. Each frame is assigned a unique numerical ‘fingerprint’, calculated by relating its own pixel value to the fingerprint of the previous frame. This means that every single image frame of the video is linked by an encryption ‘chain’ with its neighbouring image frames. The encrypted chain is stored as part of the video data when the video is recorded or exported as a video clip. Before playback, in terms of Chained Fingerprint, IDIS ClipPlayer scans video and recalculates the fingerprint chains of the video data. If any part of the image frame is tampered with, the fingerprint chain will be broken and will not match the chain value calculated at the time of video export, prompting a flag.
“As organisations look to upgrade or invest in new video solutions, protecting themselves against claims of video evidence tampering should be high on their priority list,” adds Peter Kim.



